How to Restrict Users from Executing Malicious Code from the Internet
Restricting users from changing security settings
To set trusted sites via GPO
- Open the Group Policy Management Editor.
- Go to User Configuration > Policies > Administrative Templates > Windows Components > Internet Explorer > Internet Control Panel > Security Page.
- Select the Site to Zone Assignment List.
- Select Enabled and click Show to edit the list. Refer to Figure 1 below. The zone values are as follows: 1 — intranet, 2 — trusted sites, 3 — internet zone, 4 — restricted sites.
- Click OK.
- Click Apply and OK.
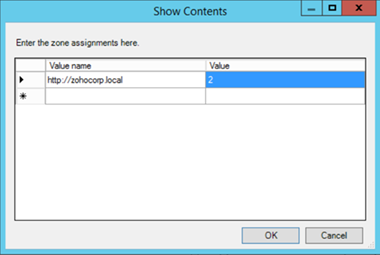
Figure 1. Assigning sites to the Trusted Sites zone.
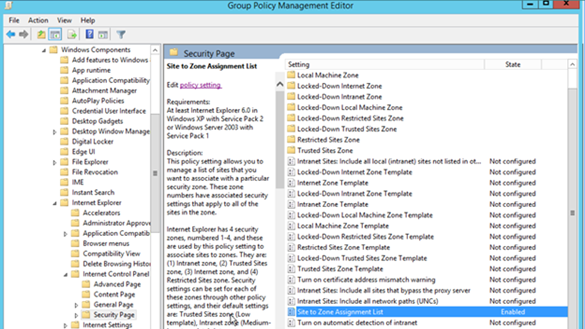
Figure 2. Enabling the Site to Zone Assignment List policy.
By enabling this policy setting, you can manage a list of sites that you want to associate with a particular security zone. See Figure 2.
Restricting users from changing security zone policies
- Open the Group Policy Management Editor.
- Go to Computer Configuration > Administrative Templates > Windows Components > Internet Explorer.
- Double-click Security Zones: Do not allow users to change policies.
- Select Enabled.
- Click
- Click Apply and OK.
This prevents users from changing the security zone settings set by the administrator. Once enabled, this policy disables the Custom Level button and the security-level slider on the Security tab in the Internet Options dialog box. See Figure 3.
Restricting users from adding/deleting sites from security zones
- Open the Group Policy Management Editor.
- Go to Computer Configuration > Administrative Templates > Windows Components > Internet Explorer.
- Double-click Security Zones: Do not allow users to add/delete sites.
- Select Enabled.
- Click
- Click Apply and OK.
This disables the site management settings for security zones, and prevents users from changing site management settings for security zones established by the administrator. Users won’t be able to add or remove websites from the Trusted Sites and Restricted Sites zones or alter settings for the Local Intranet zone. See Figure 3.
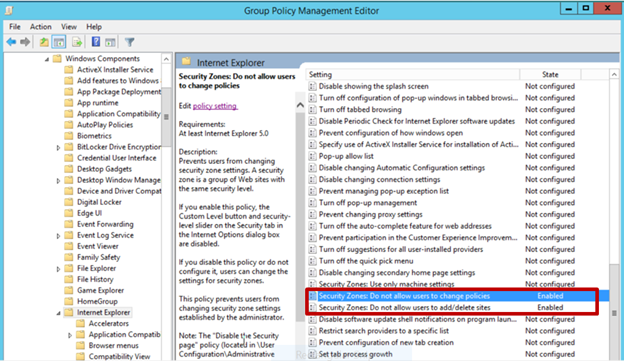
Figure 3. Enabling Security Zones: Do not allow users to change policies and Security Zones: Do not allow users to add/delete sites.
Removing the Security tab
The Security tab in Internet Explorer’s options controls access to websites by applying security settings to various download and browsing options, including defining security levels for respective security zones. By removing this tab, users will no longer be able to see or change the settings established by the administrator.
- Open the Group Policy Management Editor.
- Go to User Configuration > Policies > Administrative Templates > Windows Components > Internet Explorer > Internet Control Panel.
- Double-click Disable the Security page.
- Select Enabled.
- Click Apply and OK.
- Click
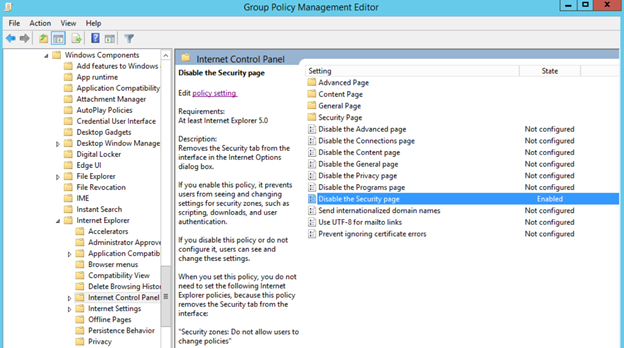
Figure 4. Enabling the Disable the Security page policy.
Enabling this policy prevents users from seeing and changing settings for security zones such as scripting, downloads, and user authentication. See Figure 4.
There’s no denying the importance of securing Internet Explorer for any enterprise. By setting security levels, restricting users from changing security zone policies, preventing them from adding or deleting sites from security zones, and removing the Security tab, users will not be able to change any security settings in Microsoft Internet Explorer that have been established by the administrator. This helps you gain more control over Internet Explorer’s settings in your environment.
Related Articles
PowerShell: How to Find Password Expiration Date for AD Users
How to get AD Users Password Expiration Date Administrators working on a Windows environment are tasked with the important job of ensuring that user accounts with soon to be expiring passwords and password expired accounts are reported and taken care ...How to Create a Group Policy to Disable USB Port for all Users except Local Administrators
How to Create a Group Policy to Disable USB Port for all Users except Local Administrators It is thus considered a safe practice to restrict USB access to all users except the administrators. This can be done with the help of Active Directory Group ...How to Delegate AD Rights to Users
Delegating Administrative Privileges to Users in Active Directory AD delegation lets administrators grant users or groups certain permissions without having to add them to privileged groups like Domain Admins and Account Operators. You can delegate ...How to create a Group Policy to Force Logoff Users
Force Logoff Users after Inactivity using Active Directory Group Policy In an organization with many user accounts, some users might forget to log off from the server. Sometimes users may be logged in long after their work has been completed. Besides ...How to Remove Users from Local Administrator Group
Removing Users From Local Administrators Group using GPO End users who are members of a Windows local administrators group will have excessive amount of privileges such as the ability to install and run programs, reset passwords, disable users, ...