Find Locked out Service accounts in Active Directory
We all have services running on our servers. Many of these services require Active Directory user accounts, which are referred to as service accounts. These service accounts are essential, as they allow services to perform their duties. However, when a service account fails to authenticate back to a domain controller, many issues can arise. If the service account fails to authenticate too many times, the user can then be locked out. Below, you’ll get a better understanding of this issue and find a better way to handle it.
What can cause a service account to fail to authenticate, and therefore lockout the user? In nearly all cases, the issue is an incorrect password. Since the password is hard coded in the service on the Windows server, the root cause is when the user account password is changed in Active Directory, but not in the service. Since many service accounts are used for more than one server or service, it can be easy to forget to synchronize passwords for one or more services.
When the service account fails even one time, the service itself will fail. Obviously, when the user is locked out due to too many failed authentications, the service continues to fail. Usually administrators are only made aware that the service has failed by receiving phone calls from users, complaining that their application does not work.
Locking out user accounts after many failed authentications is a configuration related to the password policy. The password policy determines the user account password structure and rules, as well as lockout thresholds. You can get your current lockout threshold for domain users by running “secpol.msc” on one domain controller in the domain. The output of theis should look like what you see in Figure 1.
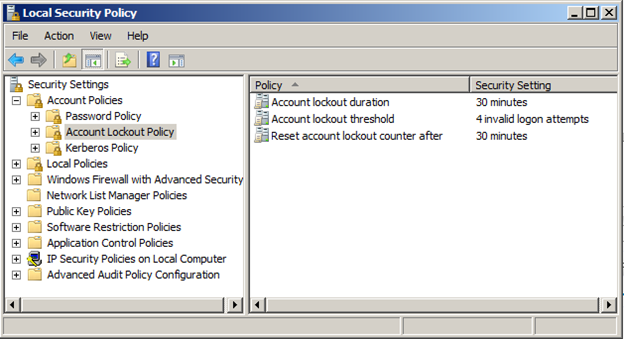
Figure 1. “Secpol.msc” reports the current lockout threshold for domain user accounts.
Finally, most administrators want a service account solution that will do two things. The first desire is to have an alert (email is ideal) associated with all service accounts. In the case of a service account password being changed and/or an account being locked out, the administrator can be informed immediately. This alert can then prevent the service from failing, and reduce calls from users complaining that their applications are not working.
Next, administrators want to be able to tie locked out users to service accounts, instead of tracking them down manually. A locked out user account can be an employee or a service account. Service accounts are very important, so it is paramount to know if they are locked out.
Related Articles
How to Change Account Lockout Policy using Group Policy Objects in Active Directory
Changing the Active Directory Account Lockout Policy Introduction to Active Directory Account Lockout Policy Account lockout policies are used by IT administrators to lock out an Active Directory account after multiple unsuccessful attempts. It is ...Simplify Service Accounts with ease | Free Service Account Manager Tool
Stop the presses! Hold on to your hats! Are you sitting down? ManageEngine has just released a new, FREE tool that will find and report all of your Windows service accounts. That is correct, you can now run a simple tool to document and get a listing ...How to Find Active Directory Accounts with Expiring Passwords
In an organization with multiple employees, it becomes tedious for the administrators to track users who's passwords are about to expire. This is crucial because, if the users fails to reset their passwords, the phone at the helpdesk is bound to ...Free AD Tool to Secure Critical Service Accounts
Service accounts carry privileges that allow them to perform actions on computers where they are configured, as well as communicate with other computers on the network. Attackers like to target service accounts due to these privileges, as well as the ...How to Find and Delete Inactive User Accounts in Windows Active Directory
Finding and Deleting Obselete User Accounts Stale user accounts in Active Directory are a significant security risk since they could be used by an attacker or a former employee to wreak havoc in your Windows environment. In addition to the security ...