Free AD Tool to Secure Critical Service Accounts
Service accounts carry privileges that allow them to perform actions on computers where they are configured, as well as communicate with other computers on the network. Attackers like to target service accounts due to these privileges, as well as the fact that many organizations do not change the password for these accounts very often. Once an attacker has obtained the credentials they need to access the network as a service account, it is nearly impossible to track and monitor their behavior. However, if you limit where the compromised service account can log on, the attacker will be restricted to only a few computers, if not just one..
In order to limit which computers a service account can log on to, you first need to know which computers the service account is configured on. For Windows services, you can use our free Service Account Management Tool to scan all of your Windows computers and identify all configured service accounts.
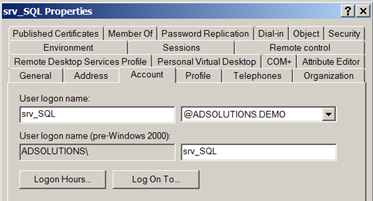
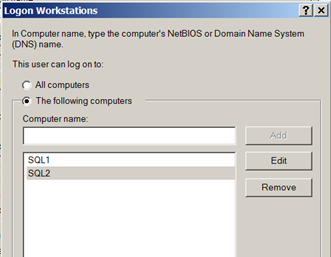
Once you have a list of which computers each service account is configured on, you can then limit the service account to only log on to those computers. To do this, you just need to go to each user account property in Active Directory Users and Computers, then configure the Log On To option found under the Account tab. Figures 1 and 2 show you what this might look like.
Figure 1. The Account tab for a user account.
Figure 2. Computers the user account can log on to.
After you configure the account settings, the user account (a service account in this case) is limited to only the computers listed. Even if the attacker obtains the credentials for this service account, they can only log on to the listed computers, substantially reducing the attack surface for these accounts.
Related Articles
Simplify Service Accounts with ease | Free Service Account Manager Tool
Stop the presses! Hold on to your hats! Are you sitting down? ManageEngine has just released a new, FREE tool that will find and report all of your Windows service accounts. That is correct, you can now run a simple tool to document and get a listing ...Detecting changes in privileged accounts in Azure AD
Monitoring and protecting privileged accounts is paramount because failure to do so can lead to loss or theft of sensitive information, or enable malware to compromise your network. Privileged accounts can include global administrators, Azure ...Find Locked out Service accounts in Active Directory
We all have services running on our servers. Many of these services require Active Directory user accounts, which are referred to as service accounts. These service accounts are essential, as they allow services to perform their duties. However, ...How to list all user accounts in the domain using Powershell
Active Directory (AD) is the backbone of user authentication and authorization in Windows environments. Managing user accounts within AD is a critical task for system administrators. PowerShell, with its robust capabilities, offers an efficient way ...List all accounts with disabled Kerberos Preauth using Powershell
Kerberos is the authentication protocol used in Windows domains to provide secure authentication for users and services. One crucial aspect of Kerberos security is preauthentication, which adds an additional layer of security to the authentication ...