Detecting changes in privileged accounts in Azure AD
Monitoring and protecting privileged accounts is paramount because failure to do so can lead to loss or theft of sensitive information, or enable malware to compromise your network. Privileged accounts can include global administrators, Azure subscription administrators, and users who have administrator access in VMs or SaaS apps.
In Azure Active Directory (AD), auditing is enabled by default. You can check all activity in any given Azure AD environment using the Azure Portal, PowerShell cmdlets, and a security information and event management (SIEM) solution.
In Azure AD, select Roles and Administrators to see the list of all available roles and their permissions. Any changes made to the accounts in Roles and Administrators can be viewed and monitored under Audit Logs as well, as seen here in Figure 1.
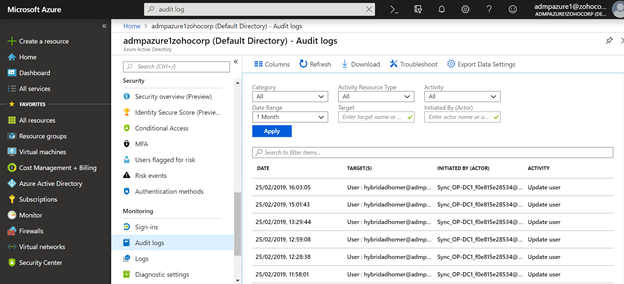
Figure 1. Audit Logs display all activity happening in an Azure AD environment.
Setting up alerts in Azure AD
Azure AD Privileged Identity Management (PIM) is a service that enables you to manage and monitor access to privileged accounts in your organization. It can generate alerts when there is suspicious or unsafe activity in your environment. When an alert is triggered, it shows up on the PIM dashboard. Select Alerts (Figure 2) to see the list of alerts generated, and select a report to see the user or roles that triggered the alert.
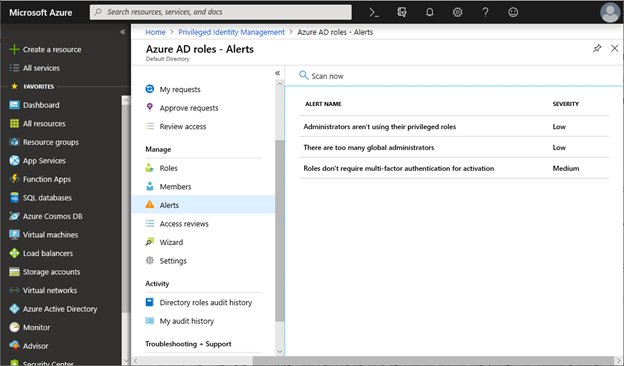
Figure 2. Alerts that are set up to monitor Azure AD roles.
To use PIM, you must have one of the following paid or trial licenses:
- Azure AD Premium P2
- Enterprise Mobility + Security (EMS) E5
If you want to set up alerts with the basic Azure AD plan, you will have to use PowerShell scripts. This leaves you with only two options; one is time-consuming and the other is expensive. The best workaround is to use a comprehensive third-party tool that is both efficient and inexpensive.
Related Articles
SSO for Azure AD Apps: Ways to Setup
Most business organizations rely on Microsoft Active Directory or it's hybrid offering, Azure AD to manage users and carry out day-to-day essential IT tasks. However, it is not uncommon to find businesses using directory services to control access to ...How to Sync On-premises Active Directory with Azure Active Directory
Synchronizing users and groups from On-premises Active Directory to Azure Active Directory Azure Active Directory is a multi-tenant, cloud-based directory and identity management service provided by Microsoft. It offers identity and access ...List all accounts with disabled Kerberos Preauth using Powershell
Kerberos is the authentication protocol used in Windows domains to provide secure authentication for users and services. One crucial aspect of Kerberos security is preauthentication, which adds an additional layer of security to the authentication ...Enable Self-service password reset in a Azure Active Directory
Enable Users to Reset Passwords using Azure Active Directory Password reset tickets constitute a major chunk of the help desk ticket pile. Allowing users to reset their own passwords is a sure way of boosting productivity. Microsoft Azure Active ...2FA for Azure AD Apps: How to Enable using Conditional Access Policies
Configuring Two Factor Authentication for Cloud Apps in Azure AD In an earlier post, we discussed in depth about how single sign-on (SSO) for cloud apps in hybrid Active Directory works and the various methods of implementing it. However, SSO alone ...